By prof. dr. Barry Derksen
At the end of January 2024, Neuralink (company of tech millionaire Elon Musk) implanted a brain chip in a man who had been paralyzed from the shoulders down for eight years at the time. Among other things, the man can now play chess (online) by controlling the cursor with his thoughts[1].
Apart from the fact that this is fantastic news for Noland Arbaugh (the person in question), it also raises a lot of questions. These concern politics, health and social issues, but also come up in our professional field. In the future, ‘human enhancement’ will also mean a lot for security, risks and privacy. After all, if people are ‘humanly enhanced’, they may also be ‘hacked’, read out for privacy-sensitive data and, going even further, remotely controlled.
The dilemma is, that it is quite predictable that by 2120 a large part of the population will make use of this ‘human enhancement’. In my opinion, there are three main reasons for this[2]:
- Health, such a Central Processing Unit (CPU) can also monitor your health and signal in time that something needs to be done (e.g. predict earlier that a cardiac arrest is coming).
- Safety, an environmentally sensitive CPU (of course in connection with sensors and ‘the cloud’) can indicate in time whether an environment is risky or not so that you can respond to it.
- Competition, if a colleague is much faster, smarter and more productive than you by using such a CPU, then the natural tendency is to at least get to the same level of play.
These three main reasons make it not a question of if it will happen, but rather when. If we use the ‘normal extrapolations’ of how fast IT, AI and robotization are going, then the only question that becomes, is how much faster than 2120 we can expect more than half of the global population to have such a CPU in their brains. At Neuralink, the first citizen of the world is already a fact.
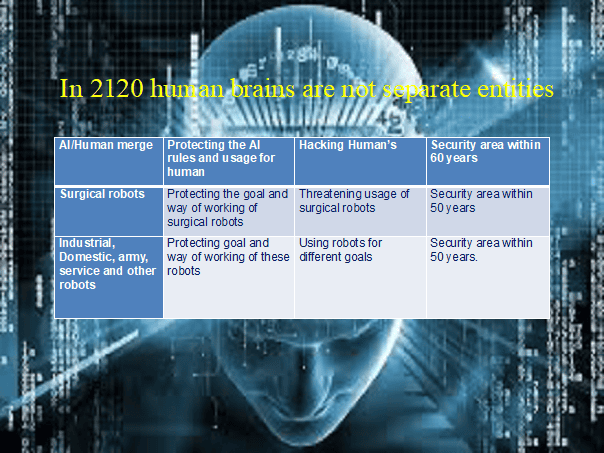
In 2120, human brains will no longer be just separate entities, but will often be merged with artificial intelligence (AI). As a result, the possibilities for humans have been considerably expanded.
Incidentally, this pattern of thinking is not new. As early as 1956, the omputer scientist John McCarthy defined artificial intelligence as “the science and engineering of making intelligent machines.”37 Almost seventy years later, the field of AI has grown tremendously and we now know it as ChatGPT, Gemini, GROK, CoPilot and the like. Serena Chen and others introduced an overview of artificial intelligence techniques. They concluded that AI techniques are increasingly being used to replace classical techniques. A few methods that are used are:
- Case-based reasoning, a type of analogous reasoning that focuses on reasoning based on previous experiences.
- Rule-based systems: systems that automate problem-solving know-how and provide a means to capture and refine human expertise.
- Artificial neural networks: these are cellular systems that are experimental knowledge.
- Fuzzy models: these are mathematical tools to represent vagueness. Fuzzy Sets are a generalization of conventional set theory that is used as a mathematical way of representing inaccuracy.
- Genetic algorithms are probabilistic search procedures designed to work on large spaces with states that can be represented by strings.
- Swarm intelligence: using the basic rules of collective behavior of a group of animals, such as ants, termites, or bees.
Coming back to our field of expertise (Security, Risk, Assurance, Privacy, Auditing), this journal of which I am proud to write the editorial takes the reader to the risks of today, tomorrow and building up to the future.
Dave van Stein and Yianna Paris revitalize IT risk strategies to be future proof. Peter Hartog introduces us to the new IIA standards in order to take the internal audit profession to an even higher level. Security compliance is denounced by Erwin Laros, Karthik Rajagopalan & Yuri Bobbert, while Martijn Timmerman and Robbert Schravendijk help us against ransomware.
In addition to these articles, Laurens Dewit, Bob Leysen and Yuri Bobbert will also look back and look ahead in response to COVID-19 in relation to cyber security strategies. And for the payback thinkers among us, we are stimulated in the thought of the biggest bang for the buck by Vincent van Dijk and Yuri Bobbert.
The ISACA NL Review Board has been reviewing the great articles of the authors in this Journal and so my thanks go to both the authors in this Journal and the review board and their constructive way of working.
On behalf of the ISACA NL Board I wish you great reading pleasure of the second ISACA NL Journal.
And P.S. you won’t see me with an enhanced human CPU any time soon…..but much can happen within 100 years from now.
Best regards,
Prof.dr. Barry Derksen
[1] https://www.ad.nl/buitenland/video-toont-hoe-amerikaan-met-hersenimplantaat-van-bedrijf-elon-musk-schaakspel-bestuurt-met-gedachten~a61e8ba0/
[2] https://www.managementboek.nl/boek/9789401810456/baseline-informatiebeveiliging-overheid-bio-gebaseerd-op-de-iso-27002-2022-barry-derksen

Barry Derksen
Member ISACA NL Board
Chairman ISACA NL Review Board


