“A practical framework for small and medium-sized businesses (SMEs) with guidelines to prevent, tackle and, if necessary, recover from ransomware attacks.”
By Martijn Timmerman & Robbert Schravendijk
Introduction
Nowadays, the functioning of many organizations is based on information and communication technology (Bada & Nurse, 2019; Camastra et al., 2011). Until recently, a lock on the door was enough to secure information such as business administration, customer base, and finances. However, SMEs are more likely to fall prey to cyber criminals. One of the biggest threats to business and government is ransomware (Yuryna Connolly et al., 2020). This article will describe the do’s and don’ts in the field of cybersecurity for SMEs based on empirical research, with a deep dive into preventing and limiting the impact of ransomware.
Changes in victimization
The Dutch economy consists largely of SMEs. These companies are also digitizing. Currently, more than 90% of all SME companies in the Netherlands are digitalized. ICT has become a (necessary) tool to continue operating profitably and sustainably (Zimba & Chishimba, 2019). However, a greater degree of digitalization among SMEs does not only have positive aspects. Cyber attacks are constantly lurking due to the degree of digitalization. Moreover, SMEs encounter difficulties in coping with cyberthreats (Van Haastrecht et al., 2021). In addition, a new cybercrime risk has emerged for SMEs; ransomware (Yuryna Connolly et al., 2020).
This article is based on empirical research into ransomware and cybersecurity among Dutch SMEs (Timmerman, 2022). The research question that was answered concerns: What are the risks of ransomware attacks for Dutch SMEs and how can they optimally protect themselves? This research was qualitative because there are limitations in the literature regarding cybersecurity, specifically aimed at SMEs. Thirteen people were interviewed. This group consisted of entrepreneurs and experts in the field of ICT and cybersecurity. Collecting in an interpretive manner allowed for an in-depth study of factors affecting cybersecurity. It was possible to analyze the human aspects of cybersecurity using Atlas. TI (software for qualitative data analysis), which is important to investigate why SMEs fall short in cybersecurity. In addition, previous research has shown the need for a more sociological analysis of cybersecurity among SMEs (Van Haastrecht et al., 2021).
Most organizations are becoming increasingly aware of these threats. However, there is a growing demand for a more specific description of how to respond to ransomware, specifically aimed at SMEs. We will therefore work step by step toward a thorough answer to the main question: What are the risks of ransomware attacks for Dutch SMEs and how can they maximize their protection? Thus, it becomes apparent what ransomware means for Dutch SMEs and how maximum protection can be achieved.
What do cybersecurity and ransomware entail?
Cybersecurity has been widely discussed in the media and business in recent years. However, finding a precise definition is difficult. Existing literature also confirms this. The research revealed that there are differences in the way the concept is viewed. A significant difference in the definition and content of cybersecurity was visible between the respondents. Among experts, there is a particular focus on information security. A participant also emphasized this:
Cybersecurity, the Dutch term we often use, is information security, which means securing your network, securing data flowing through it, and data within your network (9).
According to the experts from the study, this definition focuses strongly on data protection, while explicitly taking the human aspect into account. To clarify, the quality of cybersecurity is not purely digital but is related to human actions. Human decisions influence the operation and quality of cybersecurity within companies.
The interconnectedness of cybersecurity and cybercrime
The human aspect goes beyond the content of cybersecurity. The relationship between cybersecurity and cybercrime depends on human actions. Cybercriminals are constantly looking for security weaknesses. This research once again shows that cybersecurity often lags behind cybercrime (Timmerman, 2022). It is harder to protect a company than to attack it. New ways to create victims are constantly being discovered, with cybersecurity in general lagging behind cybercrime. A striking outcome of this research is the growth in professionalism of cybercrime. To increase the success rate, cybercriminals combine different types of cybercrime to be more successful. The social engineering aspect is also being used more and more often. This involves trying to get an employee of a company to make a human error to gain access to the IT systems.
What are the characteristics of ransomware?
Ransomware is a specific type of malware that allows cybercriminals to hack IT systems, encrypt data, and decrypt them after paying a sum of money (Baek et al., 2018). Moreover, this type of malware makes use of sophisticated social engineering tactics to gain profit (Ma et al., 2022). In principle, all companies, organizations, and private individuals can become victims of ransomware. Since larger organizations are taking more and more measures, attention is shifting to SMEs. They have less knowledge and options to protect themselves, which means the success ratio is higher for criminals. There are different variants. For example, an organization can be extorted by a teenager in an attic room or by a professional criminal organization, including a helpdesk and a crypto payment portal.
No matter how tempting it is, the advice is never to pay (Timmerman, 2022). Paying a ransom may result in the return of data, but this will finance an attack on subsequent victims. Moreover, the payment confirms the perception among cybercriminals that this type of crime pays. Paying a ransom does not guarantee that you will regain access to the hostage data (Al-rimy et al., 2018). Moreover, without adequate recovery measures, the data can be held hostage again in the future and the unscrupulous hostage taker can still offer the data for sale on the dark web. The latter is called double extortion, because the data is not only held hostage but also made public. This new method of double extortion is more visible and increases the chance of success of a ransomware attack.
A typical ransomware attack
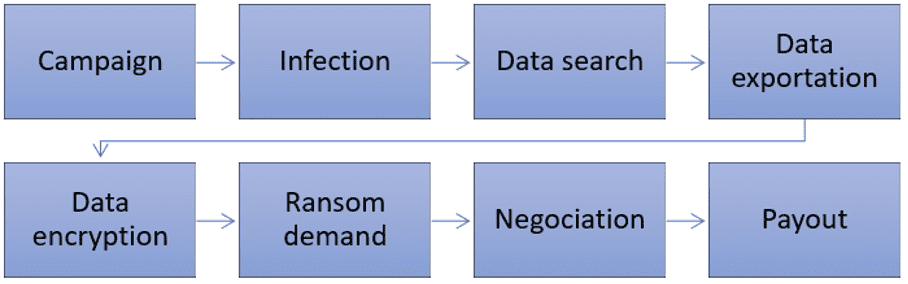
A typical ransomware attack consists of many different steps (Al-rimy et al., 2018; Sharmeen et al., 2020). First of all, a suitable company will have to be found. This company as a victim will then be analyzed in detail. Consider the turnover, which IT systems are used, what data they have, and who the employees are. After this, the ransomware attack can begin. An attempt will be made to prevent an infection from occurring. If everything goes according to plan, the cybercriminals are now in. An investigation will take place into which data can be used for extortion, such as confidential data or data that is necessary for business continuity such as planning. This data will be exported to the cybercriminals’ servers so that it can later be returned or traded. The data, the company’s systems, or both will be encrypted.
So far, if all goes well, the victim has not noticed anything. The actual attack can now take place. The systems are shut down and the company receives a notification that they have been hacked. This can be in the form of a notification on computer screens or via a telephone call. An explanation will be given of what happened and how everything can be reversed. This all sounds a lot like a hostage situation. The choice now lies with the victim. Am I going to pay, negotiate, or pay nothing? The goal of the attack, and also the final step, is an eventual payoff.
Cybersecurity is the Achilles heel of SMEs
SMEs are easy victims of cybercriminals. Cybersecurity costs money and the costs increase exponentially compared to the security achieved. Moreover, SMEs are more likely to spend money on increasing turnover than on cybersecurity. Competition among SMEs is fierce. People often think: “Why should I spend money on a password policy, that only costs time?” The growth of the company is central, and little thought is given to cybersecurity. Notably, research has shown that some SMEs are even completely unaware of cybercrime and why they may be susceptible (Timmerman, 2022). Moreover, limited resources of SMEs account for marginal investments in cybersecurity (
Confidence in the standard security of hardware and software is also too great. Sound security is assumed for used devices. However, consumer products are rarely built with cybersecurity in mind. With the growing emergence and use of the Internet of Things (IoT) and its limited security, SMEs will become even more vulnerable in the future. The false sense of confidence is also broader. Some respondents from recent research (Timmerman, 2022) were critical of the government. They believed that the government should do more to protect them against cybercrime.
How can an SME protect itself with the cybersecurity ransomware framework?
Too often it is thought that cybersecurity is purely about technical measures relating to software and hardware in ICT systems (Timmerman, 2022). However, this is not the first step that needs to be taken. The following paragraphs discuss step-by-step how an SME can improve cybersecurity and better protect itself against a possible ransomware attack.
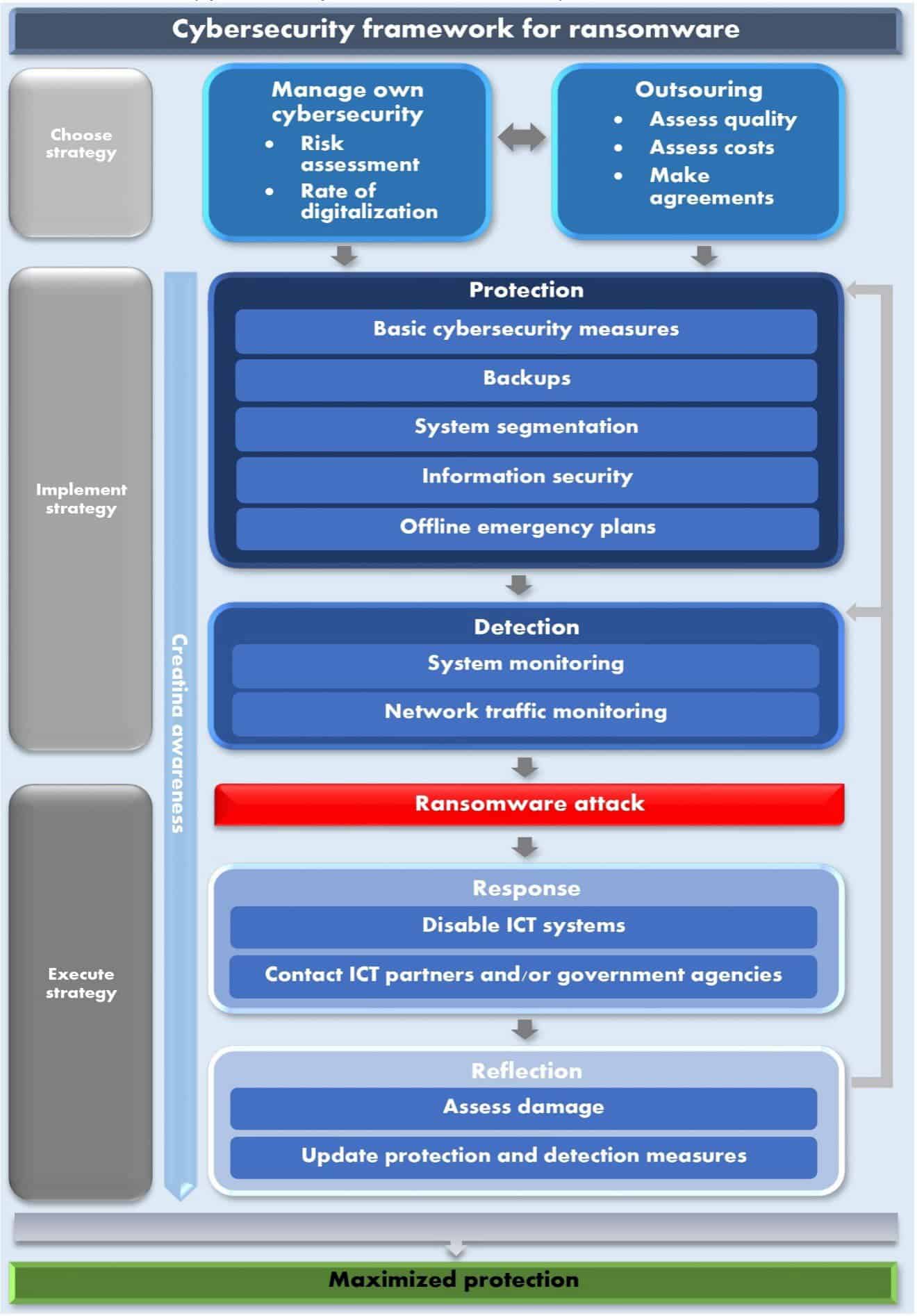
Phase 1 – Choosing a strategy
Sound protection against ransomware starts with choosing a strategy. A distinction can be made between two strategies: insourcing or outsourcing.
Strategy 1: Insourcing
First of all, cybersecurity can be arranged entirely yourself, insourcing. Good basic protection is achieved by making a risk assessment of the company. In this way, it is mapped out how vulnerable a company is to cybercriminals. Consideration should be given to questions that mainly relate to data protection and privacy. Another factor in basic protection is the degree of digitalization. The dependence on ICT determines the consequences of a cyber attack on a company. The more digitized, the more vulnerable a company becomes.
Strategy 2: Outsourcing
Nowadays companies can choose how they implement their ICT. This can be done by the entrepreneur himself, but it can also be outsourced. The rapid digitalization of SMEs has also created all kinds of ICT service providers. However, quality is not always guaranteed. It often happens that the service provider is attacked, resulting in the IT systems of their clients being paralyzed, not to mention potential data loss. It is difficult for SMEs to separate the wheat from the chaff when they look for a (new) ICT service provider. That is why it is essential to carefully find out what the quality of an IT service provider is. Clear agreements must also be made about services and crises, should they arise. Of course, costs are also important, especially for smaller companies. ICT outsourcing is expensive, especially if quality is chosen. That is why we will elaborate on measures that SMEs can implement themselves because this is more feasible for this target group.
Phase 2 – Realizing the strategy
The next step is to implement the strategy. A clear distinction must be made here. Detecting ransomware is more appropriate for outsourcing, although larger SME companies sometimes have IT professionals who can also take on this task. The protection will therefore be discussed in more detail.
Protection
Although cybersecurity is a broad concept that is often considered intangible, there are some measures that many SMEs can implement without too much effort and expense. Some adequate basic measures are a solid starting point.
Essential basic measures include a wide range of measures. First of all, having good quality antivirus software is important. Invest in decent software, not just a free trial version. These are too risky and may not detect all malware. Another important measure is the password policy. Passwords are often far too simple and can be guessed. Moreover, the same passwords are used for different purposes and are rarely or never changed. Having a password manager is recommended, for example with the Microsoft authentication app.
A basic measure that is often forgotten is awareness. Employees must know about cybercrime, at least the most common forms such as ransomware. Providing this knowledge does not have to be difficult, but it can lead to a much lower risk of infection.
However basic measures against ransomware are not sufficient. Backups are essential to prevent/minimize data loss. However, this needs further consideration. Backups should be made regularly. Furthermore, it is advisable to segment the network to minimize infection.
Segmentation plays a broader role in protection. Segmenting systems means that an infection with malware does not affect all systems simultaneously. Consider, for example, segmenting Wi-Fi networks. Customers who visit a company can also make a mistake and infect the network, whether consciously or not.
Information security should not be forgotten. Companies must be aware of what information they have. They must also consider who has access to this information.
As a final protective measure, we focus on having offline plans for crises. If the ransomware attack is so successful that all IT systems are paralyzed, it is important to know what needs to be done. Therefore, make sure you have backup plans on paper.
Detection
Although the aforementioned protection can often help a lot, there are other options for improving cybersecurity. However, these measures are more difficult, which means that adequate knowledge of ICT is necessary. Monitoring systems are essential for detecting malware infection. Unusual activity on systems and increased processor load may indicate a cyber-attack. Monitoring the network can also help detect a ransomware attack. Data traffic can be monitored, potentially leading to the discovery of unusual activity. For example, high activity can be detected at odd times when there is no business activity. Although this measure is expensive and provides knowledge, it is very effective in detecting potential cyber-attacks, not only by ransomware.
Phase 3 – Executing the strategy.
Now the time has come for a ransomware attack to take place. Unfortunately, the security/detection was not good enough. Therefore, careful consideration should be given to the response and reflection of a ransomware attack.
Response
First of all, it is important to switch off all IT systems. Perhaps the cybercriminals have not yet finished their attack and this can prevent more damage from occurring. This can be done easily for the average SME. However, nowadays a company is often dependent on ICT. Business continuity will therefore take a hard hit, especially because it may take a long time before everything can be restored.
When an SME is the victim of a ransomware attack, it is important to contact government agencies. The Digital Trust Center is a specially developed institute that can help companies with cyber attacks. Moreover, it is important to file a report. If possible, a perpetrator can be found and it will also become clearer what the annual impact of cybercrime is in the Netherlands.
Reflection
A damage assessment is essential to see how much business continuity has been affected. Data loss also needs to be analyzed, especially when dealing with personal customer data. Because SMEs often have little time for a sound ICT policy, it may not be clear exactly what data has been lost. This is why the quality of reflection after a cyber attack also depends on the degree of protection and the quality of the use of ICT.
As the final step in the framework, it is necessary to update the protection and detection measures after a cyber attack. This can prevent a company from quickly becoming a victim of a ransomware attack again. Sometimes cybercriminals attack the same victim multiple times because they know where the weaknesses are. If the SME is not aware of the weaknesses or the necessary updates in protection and detection, it is advisable to hire a professional.
These previously discussed measures are all visualized in the framework (Figure 2). The different phases of cybersecurity implementations are visible, as well as appropriate measures. This framework has been developed based on the interviews conducted and the results obtained from them.
Increasing attention to cybersecurity yields benefits
Until recently, the effects of cybersecurity were difficult to see. The benefits of cybersecurity are difficult to measure. In the Netherlands, this remains unclear. However, positive developments can already be seen in the United States, specifically concerning ransomware victimization. This level of victimization fell in 2022 for the first time in years. This is due to the growing attention to cybersecurity and its proper implementation. Larger companies are generally more likely to do this, as this involves significant costs. When larger companies become more difficult to hack, cybercriminals will focus (even) more on SMEs.
How can the government contribute to sound cybersecurity?
Although cybersecurity is a company’s job, SMEs sometimes see this differently. In particular, SMEs who have less knowledge about this subject feel that they are not sufficiently informed. So they do see the government as being responsible in some way. Only a few respondents went further, requiring more action from the government. Experts see this responsibility differently. They believe that companies are entirely responsible and that this has become part of policy in the 21st century. There are calls for the introduction of a quality mark that indicates to company customers whether a company has its cyber security in order. The research has explained this in detail, showing that SMEs and experts think differently. SMEs are positive and would like to see more clarity from companies they trade with. Experts are critical and expect problems with control, costs, and timeliness of such a cybersecurity quality mark.
Theoretical and practical implications
Based on qualitative research, more knowledge has been gained about a hitherto little-researched focus group in the study of cybersecurity; SMEs. Moreover, this research has a sample with both respondents directly from SMEs and experts in ICT and cybersecurity. In this way, a better understanding of cybersecurity and ransomware among SMEs was possible. Furthermore, cybercrime is a rapidly developing phenomenon, which may limit the applicability of older publications (Kesari et al., 2017). It is therefore important to continuously investigate this phenomenon. As a final theoretical implication, we would like to emphasize that cybersecurity studies are often limited to the United States. This research therefore addressed cybersecurity from a different geographical context.
Besides theoretical implications, it is important to achieve sound practical applicability. This research offers SMEs various cybersecurity measures that can help increase their protection against cybercrime in general and against ransomware in particular. The data from this research indicate that there is still much to be gained in the field of knowledge within SMEs in the field of cybersecurity and cybercrime. In addition, based on the results of this research, a framework has been drawn up that can provide a practical guide for improving cybersecurity within SMEs.
Conclusion
The development of cybercrime and cybersecurity are closely linked, both aiming for the discovery of technical or human shortcomings in cyberspace. (Timmerman, 2022)
Cybercrime and cybersecurity do not stand still and play a continuous cat-and-mouse game. Cybercriminals are constantly looking for new opportunities to make victims as easy as possible. For example, there are cyber-attacks in which different combinations of cybercrime are used. This allows cybercriminals to increase their chances of success.
For SMEs, the tension between the increasing attention of cyber criminals and the limited time and budget that SMEs have for cybersecurity is worth noting. An important rule of thumb is that security is always too much and too expensive until the day it turns out to be insufficient. Although resources are generally limited among SMEs, prioritization together with an early integration of cybersecurity can mitigate the risks of victimization. It is important to constantly reflect on the state of cybersecurity within the company. Keeping knowledge and awareness up to date is essential, together with modernizing ICT systems. Only in this way can the risk of victimization in the future be reduced.
References
Al-rimy, B. A. S., Maarof, M. A., & Shaid, S. Z. M. (2018). Ransomware threat success factors, taxonomy, and countermeasures: A survey and research directions. Computers & Security, 74, 144-166.
Bada, M., & Nurse, J. R. (2019). Developing cybersecurity education and awareness
programmes for small- and medium-sized enterprises (SMEs). Information & Computer Security, 27(3), 393–410.
Baek, S., Jung, Y., Mohaisen, A., Lee, S., & Nyang, D. (2018). SSD-Insider: Internal Defense of Solid-State Drive against Ransomware with Perfect Data Recovery. 2018 IEEE 38th International Conference on Distributed Computing Systems (ICDCS).
Camastra, F., Ciaramella, A., & Staiano, A. (2011). Machine learning and soft computing for ICT security: an overview of current trends. Journal of Ambient Intelligence and Humanized Computing, 4(2), 235–247.
Kesari, A., Hoofnagle, C., & McCoy, D. (2017). Deterring cybercrime: Focus on
intermediaries. Berkeley Tech. LJ, 32, 1093.
Ma, Y., Chen, J., Kuo, W., & Chen, Y. (2022). AI@nti-Malware: An intelligent framework for defending against malware attacks. Journal Of Information Security And Applications, 65, 103092.
Sharmeen, S., Ahmed, Y. A., Huda, S., Kocer, B. S., & Hassan, M. M. (2020). Avoiding Future Digital Extortion Through Robust Protection Against Ransomware Threats Using Deep Learning Based Adaptive Approaches. IEEE Access, 8, 24522–24534.
Timmerman, M. F. (2022). Defining effective cybersecurity measures for Dutch SMEs (masterthesis). Vrije Universiteit.
Van Haastrecht, M., Yigit Ozkan, B., Brinkhuis, M., & Spruit, M. (2021). Respite for SMEs: A Systematic Review of Socio-Technical Cybersecurity Metrics. Applied Sciences, 11(15), 6909.
Yuryna Connolly, L., Wall, D. S., Lang, M., & Oddson, B. (2020). An empirical study of
ransomware attacks on organizations: an assessment of severity and salient factors
affecting vulnerability. Journal of Cybersecurity, 6(1).
Zawaideh, F. H., Abu-Ulbeh, W., Mjlae, S. A., El-Ebiary, Y. A. B., Al Moaiad, Y., & Das, S. (2023, October). Blockchain Solution For SMEs Cybersecurity Threats In E-Commerce. In 2023 International Conference on Computer Science and Emerging Technologies (CSET) (pp. 1-7). IEEE.
Zimba, A., & Chishimba, M. (2019). On the Economic Impact of Crypto-ransomware Attacks: The State of the Art on Enterprise Systems. European Journal for Security Research, 4(1), 3–31.
About

Martijn Timmerman
Martijn Timmerman MSc is a master student in Information Sciences at Radboud University Nijmegen, specializing in security and privacy. He received a bachelor’s degree in Public Administration and Organization Sciences and a master’s degree in Business Administration from VU University Amsterdam, with a specialization in strategy and organization. He is interested in ICT strategy development, cybersecurity, and cyberprivacy. Contact via martijn@carpentarius.com or https://www.linkedin.com/in/martijntimmerman/.

Robbert Schravendijk
Drs. Robbert Schravendijk MMC CISM CDPSE works as an independent program manager/advisor. He has experience in setting up and transforming organizations in the areas of governance, sourcing, and risk. He is also affiliated with the Faculty of Business Administration of the VU University Amsterdam, department of Strategy & Organization. Contact via r.schravendijk@gmail.com or https://www.linkedin.com/in/robbertschravendijk/.


