By Mirjam Moerkamp and Barry Derksen
On the 23rd of May 2024, the Dutch Chapters of ISACA, ISC2 and OWASP together with the Secure Software Alliance (SSA) hosted a successful fully booked First Edition of Cyber Booked, a unique event showcasing predominantly Dutch authors of Cybersecurity books. The turnout was great, and everybody was excited to learn from the authors!

This First Edition featured Bart de Best (Continuous Security), Bram de Bruijn (Security Innovation Stories), Brenno de Winter (Survival Gids voor de Digitale Jungle), Chris van ‘t Hof (Helpende Hackers and Cyberellende was nog nooit zo leuk) and Tiago Teles (Emerging Tech, Emerging Threats).

In parallel sessions, Bart and Tiago kicked-off the presentations. Bart discussed his book in the context of the 15 books of his Continuous Everything suite. In his presentation he addressed the questions: how can you integrate continuous security in your DevOps way of working (WoW) and how does continuous security keep an organization in control?
According to Bart, to integrate security into the DevOps way of working, we need to transform the Information Security Management System (ISMS) into an Information Security Value System (ISVS). Continuous security, once integrated into the DevOps way of working, increases the security control frequency and shortens the time to market through increased deployment frequency. It also supports control by design ensuring controls are built in to mitigate risks supporting the automation of evidence enabling continuous monitoring and auditing. Bart extensively described a lot of variables concerning continuous security within the DevOps cycle. Security architecture principles, security practices, governance and continual improvement are important for the integration into DevOps WoW as discussed by Bart during the presentation (see picture below).
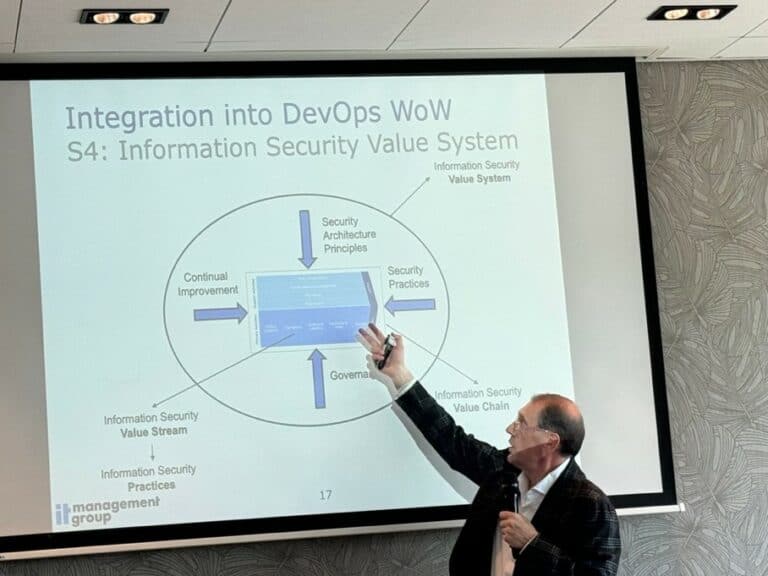
Tiago gave an interesting presentation on emerging technologies using references to technologies introduced in the past and how we predominantly tend to be wary of these new innovations. The introduction of the automated lift for example was met with apprehension and distrust given that passengers had always relied on manually operated lifts. Over time, this distrust was replaced with confidence. The same apprehension can be seen with regards to autonomous vehicles c.q. self-driving cars. Emerging technology like Artificial Intelligence can be broken down into what he referred to as “the Good, the Bad and the Ugly”, the potential of these technologies can be beneficial to us, but they also introduce potential dangers and vulnerabilities. One of his statements, that really stuck with me, is that the pace of change or technology has never evolved as rapidly as now, yet it will never be this slow again.

After the coffee break, Bram and Brenno were up. Brenno captivated the audience with his presentation on how to survive the digital jungle. With great historical facts and present-day examples Brenno helped the public feel the importance of protecting what we have and know. Assuming safety is not possible as, for example, the Titanic example (picture) taught us. And, although Brenno likes cats, most of the examples with respect to protection were given using zebra’s (zebra’s work together, some can drink while others are keeping watch in order to protect the herd). Brenno also warned the audience that new technology can be misused, e.g. a full self-driving car can also carry a bomb to a predetermined place. Finally, expect the unexpected, referring to The Black Swan by Nicolas Taleb, 2008., such as the COVID epidemic which rapidly changed the world we live in.

In parallel, Bram shared insights from his book based on 20 interviews with experts in the field. He explained that the Netherlands is losing its frontrunner position in innovation (according to the National Cyber Power Index 2022 in comparison to 2020). Innovation doesn’t necessarily have to be something disruptive or radically new. It can also be incremental or sustaining (with low technology newness but increasing impact on the market). One of the insights he discussed is that the market is still immature. As a result, customers experience solution uncertainty, which limits the adoption of new solutions. This is triggered by the control paradox and FUD (Fear, Uncertainty and Doubt). It was an interactive session with the audience sharing their own ideas and experience with respect to the insights.

Chris van ‘t Hof was our closing keynote speaker. He wrapped up the evening with an engaging presentation on coordinated vulnerability disclosure, the subject of both his books. He talked about how the Netherlands became one of the first countries to release a guideline on vulnerability disclosure and how the government is open to hackers if they do it for good. Cracking codes dates as far back to the time when Alan Turing cracked Enigma and even further back to medieval times. He also discussed the three underlying principles of responsible disclosure: societal need, proportionality and subsidiarity using examples from the past such as the Diagnostiek voor U case. These three principles also form the DIVD Code of Conduct. The Dutch Institute for Vulnerability Disclosure (DIVD) was established in 2019 and uses a platform to continuously scan for vulnerabilities and report any findings to the owners of the systems. DIVD ‘aims to make the digital world safer by reporting vulnerabilities we find in digital systems to the people who can fix them’. Bottomline, hackers see things differently and help organizations improve their security by uncovering and reporting vulnerabilities they find.

After the event, there was plenty of time for drinks, meeting & greeting the authors and book signing! All in all, a very successful evening and we look forward to organizing a Second Edition in 2025!

Mirjam Moerkamp
Mirjam Moerkamp CISSP is an ISACA NL board member.

Barry Derksen
Prof. dr. Barry Derksen is an ISACA NL board member and chairman of the ISACA NL Review Board.



