A novel approach adapted from accounting
By Yuri Bobbert
The number of enterprises subject to regulatory requirements has increased significantly under existing and new legislation such as the EU General Data Protection Regulation (GDPR), the Security of Network and Information Systems (NIS) regulations NIS1 and NIS2,[1] and the EU Digital Operational Resilience Act (DORA).[2] Last week Mario Draghi warned these EU legislations are “killing our companies”.[3] Likewise, cyberrisks adds complexity for business owners, investors, financiers, necessitating more thorough due diligence regarding an enterprise’s technology stack. Supervisory bodies will face significant challenges due to talent- and knowledge scarcity and an old-fashioned way of working. Proactive in-control statements put the burden of digital-assurance proof on the company rather than the supervising bodies. I expect this will significantly relieve both entrepreneurs and supervisory bodies.
What Is the Problem, and Who Is Affected?
Regulatory and industry requirements related to cybersecurity are skyrocketing. They include standards imposed by De Nederlandsche Bank (DNB), DORA, the European Union (EU) Cyber Resilience Act,[4] NIS2[5], the SWIFT Customer Security Programme (CSP),[6] US Federal Risk and Authorization Management Program (FedRAMP)[7], International Organization for Standardization (ISO) standard ISO 27001, the Center for Internet Security (CIS) Critical Security Controls[8], the US Federal Information Security Management Act (FISMA),[9] the National Institute of Standards and Technology (NIST) Special Publication (SP) 800-53[10], Cloud Security Alliance Capability Assessment Model (CSA CMM)[11], American Institute of Certified Public Accountants (AICPA) Trust Service Criteria (TSC)[12] and the Payment Card Industry Data Security Standards (PCI DSS)[13] etcetera. Managing all these regulations is a complex process for enterprises and regulators who need to supervise their correct implementation. The number of enterprises affected in the European Union alone runs into the millions (Figure 1).[14]
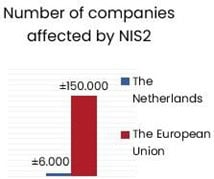
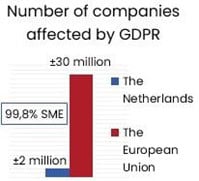
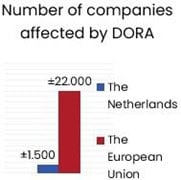
As the EU GDPR demonstrates, the necessary paperwork to demonstrate “paper-based compliance” can be done. Still, the difficulty lies in implementing the right technology and sufficient processes, capabilities (people and skills), and structures to adequately monitor and report on an enterprise’s well-being. A startup or scale-up technology company that wants to conduct business throughout Europe and the US is subject to three or more different regulations in most cases. And if they weigh the European regulatory burden against the “open US market with fewer regulations,” the choice is clear. One out of every three EU Unicorns moves from the EU to the US for this reason.[15]
Regulatory fines are often the most significant cost when something goes wrong, such as a breach or leakage. They can be as high as 4% of the annual global revenue of the violating enterprise. According to Kuijper (2020)[16], “The data privacy authorities (DPAs) mainly fine the visible symptoms of GDPR non-compliance (the materialised risks) rather than fining and describing the underlying root cause(s) of those non-compliance symptoms like, e.g., failing to analyse the data processing risks, a lack of governance or controls, etcetera.” [17]
Kuijpers research has found that most EU GDPR violations relate to implementing the technical and organizational measures required to ensure information security (Article 32). Implementing information security controls is cumbersome for many enterprises due to scarce resources and limited capabilities. Recently Antwerp Management School (AMS) researcher confirmed this by a thorough analysis of root causes of GDPR violations[18].
Upcoming regulations can only be sustained by requiring mandatory proactive submission of so-called ‘in-control statements’. Given the number of regulated companies and the associated burden, we foresee an inverse burden of proof as the only way forward: companies must be able to prove that they comply[19].
Solutions for both Regulators and business owners
Using so-called in-control statements is recommended to demonstrate you are in control over your tech environment. These statements provide a quick overview of the status of controls in a privacy and security management system. In highly regulated environments such as finance, in-control statements are already common. They can verify and demonstrate to a supervisory authority that an enterprise’s accounting has been conducted truthfully and lawfully. In-control statements are useful tools because they save supervisory authorities time, resources, and money. These statements can be checked automatically via AI technologies, similar to tax report procedures, and report outliers or deficiencies. Periodically, a manual audit assesses whether an enterprise has provided truthful information, and the accountable persons must sign off on the findings.
Every framework doesn’t need to have its own in-control statement. There is often a certain amount of overlap in the controls they propose. This overlap can be mapped to understand where the frameworks coincide. For example, one parent framework may correspond with multiple child frameworks and their controls. Testing for control in the parent framework ensures compliance with multiple other underlying controls—the “test once, comply many” principle (Figure 2). This mapping, which is done by entities such as Secure Controls Frameworks, is already present in technology such as Anove and is updated every time there is a change in the framework[20]. This allows enterprises to submit just one in-control statement that attests to their adherence to many frameworks.
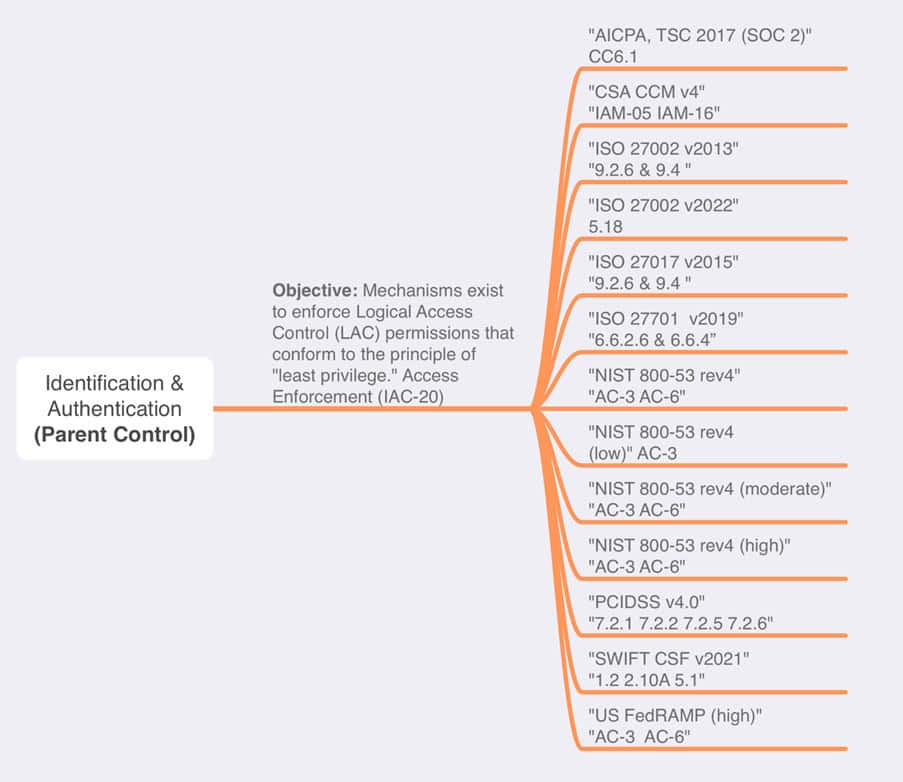
Good Governance
Complying with all applicable regulations while implementing proper security management is a challenge. One way to navigate this complexity is to use an existing framework as the basis for managing cybersecurity, whether within a specific country or within a specific industry. For example, when the United States experienced a major attack on the Colonial Pipeline[21], using NIST 800-053 and zero-trust strategies (NIST 800-207) became mandatory after a presidential executive order. Europe is moving in the same direction, taking a similar top-down approach to digital security. This is comparable to what happened after the MCI WorldCom[22] and Enron[23] accounting scandals, which led to the directive of the Sarbanes-Oxley Act (SOX)[24] in the United States to improve auditing and public disclosure requirements. In both cases, chaos led to clear mandates to implement controls and processes and standardisation in reporting In essence, treating cybersecurity management in the same way as financial reporting standards ensures a structured and comprehensive approach that provides monitoring that can detect deviations or malfunctions. It also encourages good stewardship among owners. Monitoring and reporting the status of the entire technology stack is crucial for any enterprise and its stakeholders, including investors, shareholders, supervisory bodies, and potential buyers. Hence, digital security is a matter of the highest executive-level decision-making. The question remains: will anyone take the lead in implementing a top-down approach to direct a foundational framework, or will an incident such as the ransomware attack on the Colonial Pipeline have to happen before any action is taken?
Future outlook
I anticipate a transformative shift towards stringent regulations mandating businesses to disclose their cybersecurity, privacy, and data security efforts with unprecedented transparency in their annual or quarterly reports, mirroring the post-Enron and MCIWorldcom era’s regulatory overhaul. I recommend that companies take proactive steps to:- Identify and comply with the specific regulatory requirements (What) they need to follow, including clear plans for how to do so (How), assign owners (Who), carry out those plans, and assess their effectiveness on periodic basis (When).
- Adopt a “Test Once Comply Many” approach with a common controls framework, to prevent redundant or overlapping work.
- Establish an operational model that promotes and enforces accountability through regular planning, implementation, and evaluations, with periodic reporting on performance. This should be enforced from the top down.
About the author

Yuri Bobbert
Yuri Bobbert PhD, is professor at Antwerp Management School, CEO at Anove.AI and CSO at ON2IT.
References
[1] Regulation (EU) 2022/2554 of the European Parliament and of the Council of 14 December 2022 on digital operational resilience for the financial sector: https://eur-lex.europa.eu/eli/reg/2022/2554/oj
[2] PricewaterhouseCoopers, “DORA: Why Is It Relevant to You,” https://www.pwc.com/gr/en/advisory/technology/dora-why-it-is-relevant-to-you.html
[3] The future of European competitiveness: Report by Mario Draghi
https://commission.europa.eu/topics/strengthening-european-competitiveness/eu-competitiveness-looking-ahead_en
[4] European Commission, “Strengthening EU-Wide Cybersecurity and Resilience—Provisional Agreement by the Council and the European Parliament,” European Union, https://www.nis-2-directive.com; European Commission, “Cyber Resilience Act,” European Union, https://digital-strategy.ec.europa.eu/en/library/cyber-resilience-act
[5] https://eur-lex.europa.eu/eli/dir/2022/2555
[6] SWIFT, “Customer Security Programme,” https://www.swift.com/myswift/customer-security-programme-csp
[7] The Federal Risk and Authorization Management Program (FedRAMP®) https://www.fedramp.gov/
[8] https://www.cisecurity.org/controls
[9] US Congress, “FISMA, U.S. Congress, Federal Information Security Management Act of 2002,” March 2002, USA, https://www.congress.gov/bill/107th-congress/house-bill/3844
[10] Security and Privacy Controls for Federal Information Systems and Organizations: https://csrc.nist.gov/pubs/sp/800/53/r4/upd3/final#:~:text=This%20publication%20provides%20a%20catalog,other%20organizations%2C%20and%20the%20Nation
[11] The CSA Cloud Controls Matrix (CCM) is a cybersecurity control framework for cloud computing.
https://cloudsecurityalliance.org/research/cloud-controls-matrix
[12] https://www.aicpa-cima.com/resources/download/2017-trust-services-criteria-with-revised-points-of-focus-2022
[13] Payment Card Industry Security Standards Council, “Payment Card Industry Data Security Standards,” https://www.pcisecuritystandards.org/document_library/?document=pci_dss
[14] BBP Media, “NIS2 Is Coming—And the Retail Industry Is Not Prepared,” 26 October 2022, https://www.bbpmedia.co.uk/business-insights/retail/nis2-is-coming-and-the-retail-industry-is-not-prepared.html; CBS, “Businesses; Company Size and Legal Form,” 2023, https://opendata.cbs.nl/#/CBS/nl/dataset/81588NED/table; Eurostat, “Sectoral Overview,” 2021, https://ec.europa.eu/eurostat/cache/htmlpub/key_figures_on_european_business_2021/sectoral_overview.html; Kors, S.; “What Does NIS2 Mean for Dutch Organizations?,” 7 December 2022, https://www.computable.nl/artikel/blogs/security/7444125/5260624/wat-betekent-nis2-voor-nederlandse-organisaties.html;
[15] In 2008 and 2021, close to 30% of the “unicorns” founded in Europe – startups that went on the be valued over USD 1 billion – relocated their headquarters abroad, with the vast majority moving to the US.: https://commission.europa.eu/document/download/97e481fd-2dc3-412d-be4c-f152a8232961_en?filename=The%20future%20of%20European%20competitiveness%20_%20A%20competitiveness%20strategy%20for%20Europe.pdf
[16] N. Kuijper, “Translation of GDPR article 32 into effective privacy governance and management practices. A view on GDPR ambiguity, non-compliancy risks and effectiveness of ISO 27701:2019 as Privacy Management System,” 12 June 2020. [Online]. Available: https://zenodo.org/records/3891540.
[17] Conijn, F.; Smit, R.; “Buyer Seizes Power in Business Takeovers,” Het Financieele Dagblad, 16 October 2023, https://fd.nl/bedrijfsleven/1493159/koper-grijpt-de-macht-bij-bedrijfsovernames
[18] G. Heiremans, “Navigating the Fine Line: Achieving GDPR Compliance while Optimizing IT Investments An investigation on how companies can evaluate the appropriateness of technical and organizational measures in light of articles 5,25 and 32 of GDPR.,” Antwerp Management School (AMS), Antwerp, 2024.
[19] Y. Bobbert, “Tech Regulations: How to Relieve the Burden of Supervisory Bodies and Reduce Risk for Investors,” ISACA, https://www.isaca.org/resources/isaca-journal/issues/2024/volume-3/how-to-relieve-the-burden-of-supervisory-bodies-and-reduce-risk-for-investors, 2024.
[20] https://www.anove.ai/blog-posts/in-control-statements-made-easy
[21] https://www.cisa.gov/news-events/news/attack-colonial-pipeline-what-weve-learned-what-weve-done-over-past-two-years
[22] https://sc.edu/about/offices_and_divisions/audit_and_advisory_services/about/news/2021/worldcom_scandal.php
[23] The Enron scandal is likely the largest, most complicated, and most notorious accounting scandal of all time https://corporatefinanceinstitute.com/resources/esg/enron-scandal/
[24] 107th US Congress, H. R. 3763 Sarbanes-Oxley Act of 2002, USA, 30 July 2002, https://www.congress.gov/bill/107th-congress/house-bill/3763/text.


