Abstract: Cyber insurance is evolving from merely compensating losses after breaches to actively fostering measurable cyber resilience. Recent studies show that current insurer questionnaires often fail to align with established cybersecurity frameworks, leading to policy mispricing and inadequate risk differentiation. Only 6–35% of assessments measure technical maturity, with most focusing on documentation. Research indicates that Zero Trust can reduce breach costs by up to 75%. Insights from the “Decoding the Future of Cyberinsurance” roundtable with U.S. insurers confirm that Zero Trust is now viewed by insurers, regulators, and financial institutions as vital for underwriting, governance, and compliance. The industry is transitioning to “Cyber Insurance 3.0,” which relies on continuous telemetry, maturity scoring, and real-time assurance instead of static compliance reports. In this new approach, premiums will be dynamically adjusted based on demonstrated control effectiveness. This article underscores that organizations capable of continuous validation, real-time dashboards, and verifiable governance will not only enjoy lower premiums but also attract greater investor confidence and enhance operational resilience.
A Market at an Inflection Point
The cyber insurance industry is at a defining moment. Once viewed as a reactive financial hedge against cyberattacks, insurance is now evolving into a proactive mechanism for managing cyber risk and rewarding verifiable resilience. Two converging forces are driving this transformation:
- The maturing of Zero Trust security principles as a measurable risk-control framework, and
- Academic research linking insurance requirements to standardized cybersecurity controls exposes a critical need for alignment between insurers and the insured.
Recent academic work at Antwerp Management School (AMS), Mapping Cyber Insurance Questionnaires to Standardized Security Controls, provides the most granular view yet of how cyber insurers assess risk. The study, led by Steve Bielen (Senior Information Security Officer) under my supervision, systematically mapped 12 underwriting questionnaires from major European insurers against the CIS Critical Security Controls. The findings are a wake-up call for both underwriters and CISOs: the alignment between what insurers ask and what actually reduces cyber risk remains partial, inconsistent, and often superficial.
From Information Asymmetry to Assurance
Cyber insurance faces the same classic economic paradox identified by Rothschild and Stiglitz in 1976: imperfect information between insurer and insured leads to adverse selection, where high-risk clients overpopulate the risk pool, driving up premiums for everyone.
The AMS research demonstrates that this asymmetry persists because insurers rely on questionnaires that are not aligned with recognized cybersecurity frameworks. Across the surveyed insurers, coverage of the CIS Controls ranged from 55% to 94%, but actual implementation depth ranged from 6% to 35%. In other words, insurers ask many of the right questions, but few assess the quality or maturity of the security measures themselves.
This is not merely academic. Poorly aligned questionnaires undermine underwriting accuracy, leaving insurers unable to price risk effectively and clients uncertain about what is truly expected of them.
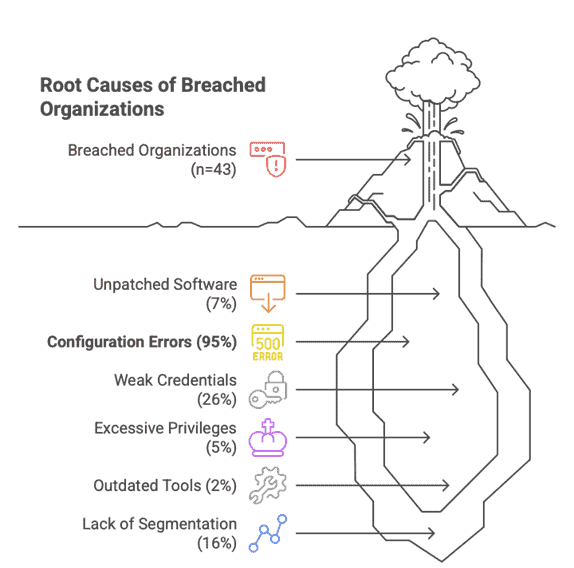
To break this cycle, insurance underwriting must evolve from checklists to control validation, from asking whether a policy exists to verifying that safeguards such as multifactor authentication, segmentation, and incident response are demonstrably enforced and monitored. To truly understand this knowing-doing gap, organisations’ insurers in a new era should shift from questionnaires to real-time telemetry of the cyberfundamental measures. Over the past 20 years, 95% of the root causes of catastrophic events have been configuration flaws—technical errors which could have been prevented by knowledge or specific expertise. And could have been detected by ingesting configuration logs, validating them against known industry best practices, and, if a deviation was noticed, informing the owner. Similarly, if a CCTV camera failed, the surveillance duty would have seen it. The results and case learnings of this study into the knowing-doing gap were published in the ISACA Netherlands Journal and visualised below:
Zero Trust: The New Currency of Insurability
In Decoding the Future of Cyberinsurance, the New York roundtable on Zero Trust in the Financial Sector revealed that the industry is now recognizing Zero Trust as the missing link between security operations and financial assurance. During the Group Support System session in July at Venable, participants agreed that Zero Trust is no longer optional; it is the operational backbone of measurable cyber maturity.
Zero Trust’s emphasis on protect surfaces, continuous verification, and least privilege directly addresses the core of cyber insurers’ risk calculus — likelihood and impact of loss. Where traditional controls fail to demonstrate real-time efficacy, Zero Trust as a Service (ZTaaS), integrating technical measures, dashboards, and incident response, provides empirical evidence of resilience. According to supporting research by Tim Timmermans and me, ZTaaS can reduce the cost of a breach by up to 75% while simultaneously lowering insurance premiums by demonstrating improved governance and incident readiness.
Key Findings Shaping the Future of Cyber Insurance
1. The Disconnect Between Frameworks and Practice
The AMS research revealed that while most insurers assess technical measures such as firewalls or antivirus software, few evaluate critical “Respond” and “Recover” functions, the very capabilities that determine loss severity. This reflects a systemic bias toward prevention over resilience. Future underwriting must account for these response-based controls, as they directly influence recovery time, regulatory penalties, and reputational loss.
2. Revenue-Based Risk Pools Are Obsolete
Grouping insured organizations by annual revenue, a common underwriting practice, ignores the realities of cyber risk. Research shows that industry type and operational exposure are far stronger predictors of loss. Manufacturing, healthcare, and finance face distinct threat models and should be scored accordingly. Risk-based segmentation using protect surface definitions and Zero Trust maturity scores will enable fairer premiums and sustainable market equilibrium. I detail this way of working with protect surfaces and their critical success factors and failures in 2022, in the paper “Perspectives from 50+ Years’ Practical Zero Trust Experience and Learnings on Buyer Expectations and Industry Promises”.
3. Zero Trust as a Shared Framework for Insurers and Insured
Both Bielens’, AMS research, and ON2IT market validation in the US call for a shared language between insurers and insureds, built on standardized frameworks like the CIS Controls and NIST CSF. This alignment allows insurers to map underwriting questions directly to known safeguards, creating transparency for clients and comparability across carriers.
4. Dashboards as the New Audit Interface
As noted during the New York roundtables, dashboards are replacing compliance reports as the new evidence layer for assurance. Real-time dashboards showing asset inventories, control effectiveness, and incident metrics provide both underwriters and regulators with live proof of the security posture, not static attestations.
5. From Reactive Payouts to Preventive Incentives
The future of cyber insurance lies in incentivizing continuous validation. Carriers will increasingly tie premium discounts or extended coverage to validated Zero Trust adoption, similar to how the automotive insurance industry rewards telemetry-based safe driving.
The Road Ahead: Cyber Insurance 3.0
We are witnessing the emergence of Cyber Insurance 3.0, an era where the policy is not just a financial instrument but a cyber risk governance mechanism. Based on insights from experts in the insurance, tech, and financial sectors, we can identify the following key additions in this 3.0 model:
- Underwriting is informed by real-time security telemetry. Gained from CISO Teams or Managed Security Service Providers (MSSP)
- Premiums are dynamically priced based on measured risk posture (per protect surface, since they can differ in value, risk they pose, and the level of security needed).
- Claims are evaluated with dashboard-based evidence, not declarations.
- Policy renewals depend on continuous compliance with Zero Trust metrics.
This shift will require insurers to invest in actuarial models that connect Zero Trust maturity and telemetry data directly to claim frequency and severity, moving from uncertainty to quantifiable risk management.
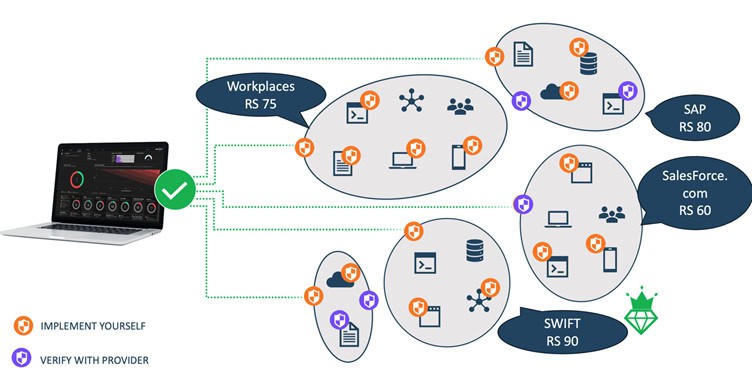
These 3.0 models, data ingestions, and visual representations already exist. See below for an example of a working technology called AUXO. When combined with the insurer’s underwriting knowledge, 3.0 is established.
Conclusion: The Path to Assurance
The future of cyber insurance will be shaped not by policy wording, but by proof of control.
Research from Antwerp Management School provides the quantitative foundation, while the Decoding the Future of Cyberinsurance roundtable offers the qualitative direction:
A market evolving toward data-driven, Zero Trust–enabled assurance.
In this emerging paradigm, insurers become enablers of resilience rather than mere financiers of recovery. Organizations that can demonstrate measurable, continuous control effectiveness will not only earn lower premiums but also greater investor confidence, regulatory trust, and market resilience. Cyber insurance will no longer reward those who survive incidents, but those who prevent them.
Used Methodology
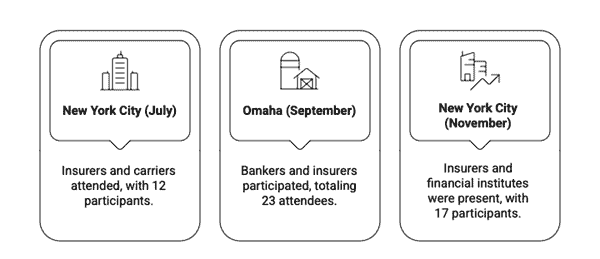
We utilized academic research data from previous studies and built upon that foundation to formulate hypotheses and questions. This aimed to validate new insights and viewpoints on how Cyberinsurance products can be enhanced. The goals included incentivizing better performance, expanding coverage, gaining actuarial data insights, and improving underwriting processes. A Group Support System (GSS) approach was used to collect, discuss, and document expert insights from professionals in finance, insurance, and technology. In total, 52 U.S.-based experts participated in the roundtable discussions I moderated.
Used Sources
Bobbert, Y., & Timmermans, T. (2025). How Zero Trust Reduces Cyber Risks and Lowers Cyber Insurance Premiums. ON2IT / Springer Nature, Future Technologies Conference 2025, Munich.
Bielen, S. (2025). Mapping Cyber Insurance Requirements to Security Controls (Master’s thesis, Antwerp Management School, supervised by Prof. Dr. Yuri Bobbert).
Bobbert, Y. Derksen, B. (2025) The Knowing-Doing Gap in Digital Security The Silent Risks of Not Validating Your Security Controls Regularly. Three Takeaways to close the gap published in ISACA Netherlands Journal.
S. Kably (2021) The Root Cause of Data Breaches Investigating security misconfigurations as the root cause of data breaches. http://resolver.tudelft.nl/uuid:40c652a8-b66a-46e1-8953-c8c90398f9ee
Bobbert, Y., & Hake, D. (2025). Decoding the Future of Cyberinsurance: Insights from the New York Roundtable. ON2IT / Venable.
Center for Internet Security. (2024, 05). CIS Controls Master Mapping. Retrieved from cisecurity.org: https://www.cisecurity.org/insights/white-papers/cis-controls-v8-master-mapping-to-mitre-enterprise-attck-v82
Center for Internet Security. (2024, June 25). CIS Controls v8.1 Mapping to NIST CSF 2.0. Retrieved from Center for Internet Security: https://www.cisecurity.org/insights/white-papers/cis-controls-v8-1-mapping-to-nist-csf-2-0
Ponemon Institute. (2024). Cost of a Data Breach Report. IBM Security.
ENISA. (2024). Threat Landscape 2024. European Union Agency for Cybersecurity.
Kindervag, J. (2010). No More Chewy Centers: Introducing the Zero Trust Model of Information Security. Forrester Research.
Pfeffer, J., & Sutton, R. (2001). The Knowing–Doing Gap: How Smart Companies Turn Knowledge into Action. Harvard Business School Press.
Bobbert, Y., & Timmermans, T. (2023) How Zero Trust as a Service (ZTaaS) Reduces the Cost of a Breach A Conceptual Approach to Reduce the Cost of a Data Breach FTC 2023, LNNS 816, pp. 433–454, 2023. https://doi.org/10.1007/978-3-031-47448-4_33
Bobbert, Y., Scheerder, J. & Timmermans, T. (2022) Perspectives from 50+ Years’ Practical Zero Trust Experience and Learnings on Buyer Expectations and Industry Promises. SAI 2022, LNNS 508, pp. 864–881, 2022. https://doi.org/10.1007/978-3-031-10467-1_53
Bobbert, Y. (2025) 10 Insights from banking CISOS on Smarter Cybersecurity Investments
Bobbert, Y. (2025). How Zero Trust is Transforming Cyber Insurance in Financial Services.
Bobbert, Y. (2025). How Zero Trust is Reshaping Cyber Insurance.
