Furthermore, NIS2 is a Directive; It is essentially an outline and set of instructions for Member States to create national legislation. Therefore, even an understanding of the Directive is insufficient to ensure compliance with European cybersecurity legislation.
Despite the complexity of the legislation, at its core the Directive requires the organizations in its scope to set up a cybersecurity program and controls. There are a number of standards and frameworks that provide similar requirements, such as the ISO 27001 and the NIST CSF. Those standards are well suited to address many of NIS2 requirements. But many is not all, and while both frameworks can be used to become compliant, there are specific considerations to ensure compliance to NIS2.
Rather than taking the grant tour of security controls that are required by the Directive, let’s focus on creating an understanding of its distinctive expectations and requirements. Acquiring that understanding not only requires a summation of controls and features specific to the legislation, but also requires an understanding of its background.
Background
On January 16, 2023, the NIS2 Directive went into effect. It’s aim is to “achieve a high common level of cybersecurity across the Union, with a view to improving the functioning of the internal market” (NIS2 article 1, paragraph 1). It requires EU Member States to draft cybersecurity legislation that promotes resilience in cyberspace operations and protects the Union’s citizens and economic welfare.
October 2024 marked the beginning of the enforcement of all local legislation adopted in line with the EU NIS2 Directive. A staggering number of over 30,000 scoped organizations in Germany alone[1], and an estimated number of over 100,000 scoped organizations operating in the EU are expected to comply with the Directive’s goals. However, nothing ever goes as planned, including the passage of legislation. Out of the 27 EU states, only Belgium, Croatia, Italy, and Latvia have managed to introduce adequate legislation on time. Since then, Finland, Greece, Hungary, Lithuania, Romania, and Slovakia have passed NIS2 legislation.[2] For organizations operating in these countries, NIS2 enforcement is a reality. Although organizations in other EU states may enjoy an extended grace period, they should be aware that when their legislation is enacted, it is likely to be enforced immediately without a transition period for compliance.
Governance and risk management requirements
The core of the Directive and the transposed national laws concerns resilience (NIS2 article 1, paragraph 1) and cybersecurity risk management (NIS2 article 1, paragraph 2). They address the Union’s concerns about the economic and societal impact that incidents originating from cyber threats may have (NIS2 article 21, paragraph 1). In essence, NIS2 requires all scoped organizations to assess their cyber risks and take appropriate and proportionate actions. In addition, the Directive provides a baseline of risk measures that these organizations must implement and operate, regardless of any risks that they have identified.
NIS2 compliance involves adhering to its 46 articles, which are contextualized through 144 recitals. Its integration into existing EU legislation results in over 140 references to other European laws, directives, and legal documentation. Therefore, it is advisable for organizations that are or may be affected by the Directive to spend adequate time gaining a thorough understanding or to participate in training that addresses the Directive’s specific requirements and expectations. In any case, members of the management bodies of the organizations in scope are required to undergo training on this topic, ensuring they acquire sufficient knowledge and skills to identify risks and assess cybersecurity risk-management practices and their impact on the services the organization provides (NIS2 article 20, paragraph 2).
Supply chain implications
While over 100,000 organizations fall directly under the scope of the Directive, even more organizations worldwide will inevitably face and need to address the implications of this Directive and the transposed laws in each of the EU Member States. This stems from the clear requirement for all scoped organizations to manage risks throughout the entire supply chain, not just with their direct suppliers (NIS2 article 21, paragraph 2d). From a security standpoint, the reasoning behind this requirement is clear, as the number of supply chain attacks is increasing rapidly (NIS2 recital 54). However, from an implementation perspective, this presents a significant challenge. It is clear that large cloud providers will not be able to assist over 100,000 organizations in providing insights into the supply chains they utilize. The Directive anticipates this and includes a provision that allows the Cooperation Group, the European Commission, and ENISA to conduct risk assessments for critical ICT services, systems, and products (NIS2 article 22). Such assessments would logically encompass a supply chain risk assessment, which can then be referenced by the organizations that fall under the NIS2 scope.
Business continuity
One of the risk management measures required by the Directive is business continuity. The Directive includes backup management, disaster recovery, and crisis management as part of this requirement (NIS2 article 21, paragraph 2c). This requirement has already led many organizations to place business continuity under the purview of the Chief Information Security Officer. Whether this is the right choice is debatable. Business continuity contains the word “Business” for a reason. It focuses on ensuring that the business can remain viable despite disruptions. While these disruptions may be related to cyber threats, the responsibility for business continuity ultimately lies with the business. Note that neither crisis management nor business continuity are considered controls in ISO 27001 Annex A. An alternative to consider, especially for organizations already certified in ISO 27001, is ISO 22301, which develops a business continuity management system following the same structure as the information security management system. Those pursuing the NIST CSF will find that this framework also lacks specifics on business continuity and crisis management. NIST Special Publication 800.34[3] and Special Publication 800.61[4] respectively address these topics.
Reporting requirements
Like GDPR, NIS2 defines very specific reporting requirements. Unlike GDPR, however, these reporting requirements not about admitting guilt and showing how you will prevent recurrence. Instead, they are defined to ensure that indicators of significant threats and incidents are made known as soon as possible and shared across the Union to help organizations avoid similar incidents. This is why NIS2 reporting requirements include a 24 hour early warning notification, a 72 hour incident reporting and a closing report describing the root cause and steps taken to prevent recurrence. For NIS2, not reporting significant incidents increases the organization’s liability. On the contrary, NIS2 article 23 paragraph 1 explicitly states that “the mere act of notification shall not subject the notifying entity to increased liability”.
Navigating the organization towards NIS2 compliance
Organizations have various obligations, including technical risk measures, reporting, and supervision responsibilities. If you are looking for a quick overview of the requirements directly affecting your organization, Articles 20, 21, 23, and 32/33 are an excellent starting point. However, to fully understand these obligations, a more thorough study is necessary. A helpful step is to attend NIS2 training, such as the two-day CNIS2 Professional training program. This training is developed and certified in the EU, which makes sense given the context of EU legislation. It presents NIS2 from a practical perspective and guides attendees through a gap assessment. More broadly, programs like ISACA’s CISM, CRISC, and CGEIT provide a solid foundation in information security, greatly benefiting anyone implementing cybersecurity risk management measures.
Using ISO and NIST frameworks to become compliant
Frameworks like ISO 27001 and the NIST CSF are well-suited for compliance with NIS2. In some transposed legislations, such as the Belgian NIS2 law, ISO 27001 is explicitly mentioned as a means to demonstrate compliance[5]. However, these frameworks must be designed with the Directive’s specific requirements and expectations in mind.
NIS2 article 21, paragraph 1 requires organizations to “take appropriate and proportionate technical, operational and organisational measures to manage the risks posed to the security of network and information systems”. Security of network and information systems is defined in the Directive under article 6, paragraph 2 as “the ability of network and information systems to resist, at a given level of confidence, any event that may compromise the availability, authenticity, integrity or confidentiality of stored, transmitted or processed data or of the services offered by, or accessible via, those network and information systems”. The definition addresses the typical Confidentiality, Integrity, and Availability elements which are addressed by common frameworks. ISO/IEC 27001:2022 paragraph 0.1 states that “The information security management system preserves the confidentiality, integrity and availability of information by applying a risk management process and gives confidence to interested parties that risks are adequately managed.” NIST CSF 2.0 also refers to these terms throughout the framework in reference to the cybersecurity risk. Neither explicitly recognizes authenticity as a factor. It does not mean that the framework are unusable, but it does mean that they require organizations doing risk management to consider authenticity of information as a factor.
When assessing risks, NIS2 states that “due account shall be taken of the degree of the entity’s exposure to risks, the entity’s size and the likelihood of occurrence of incidents and their severity, including their societal and economic impact”. Organizations pursuing ISO 27001 certification are expected to assess the impact of risks. Impact is specified in ISO 31000:2018 paragraph 6.4.2 as “impact on objectives”. Consequently, many organizations following standards like ISO 27001 only consider factors that impact their organizations directly and, unless the organizational objectives include servicing society or the EU, they will most likely not consider societal and economic impact factors when determining risk acceptance. In order to comply with the Directive, organizations must consider these factors explicitly as part of the impact of risk.
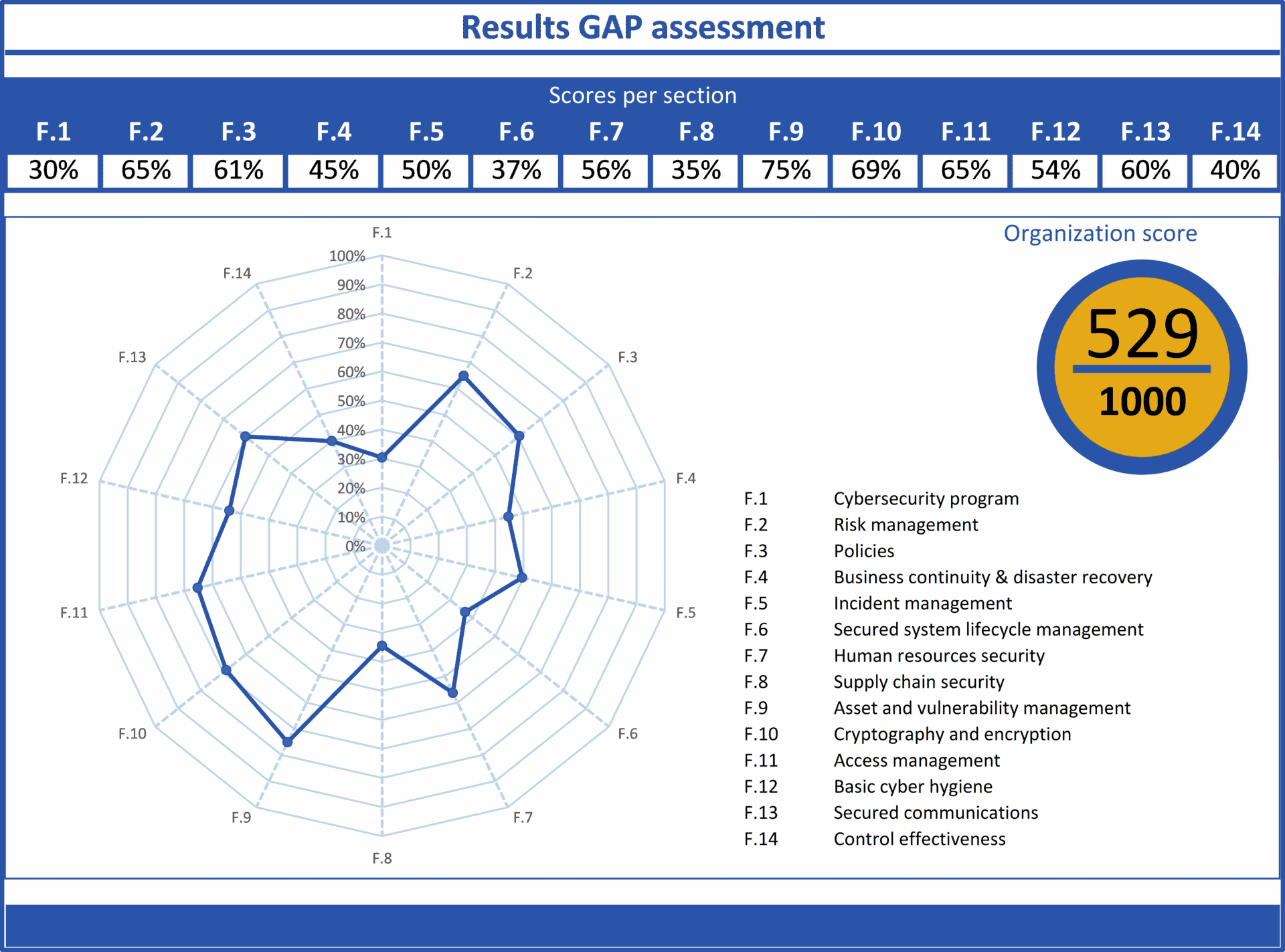
The GAP assessment
No matter how knowledge is acquired, and regardless of whether you have implemented any frameworks already, the starting point for a NIS2 compliance program is a gap assessment. This assessment provides an overview of the existing gaps within the organization’s current state and the required NIS2 compliance. The multilingual tool included in the NIS2 Navigator’s Handbook[6] also suggests treatment steps and references relevant sections in the book for each identified gap.
A gap assessment can serve as a valuable reporting mechanism, allowing security professionals to update members of management bodies on progress toward compliance. Additionally, this reporting functions as a compliance measure, demonstrating management’s oversight of the implementation of risk management measures.
NIS2 compliance action list
The NIS2 Directive introduces a significant change for organizations falling under its scope as well as a number of organizations not immediately in its scope. Rather than approaching this in an ad hoc manner, take a structured approach and create a program around its implementation and continuing operations. The table below provides a potential plan of steps you can take.

[1] https://www.isico-datenschutz.de/en/article/nis2-directive-scope-requirements-actions
[2] Source: https://ecs-org.eu/activities/nis2-directive-transposition-tracker/
[3] https://www.nist.gov/privacy-framework/nist-sp-800-34
[4] https://www.nist.gov/privacy-framework/nist-sp-800-61
[5] Source: https://ccb.belgium.be/recent-news-tips-and-warning/adoption-nis2-royal-decree
[6] https://amzn.eu/d/gsbKI6k
